What is eBPF?
eBPF, or Extended Berkeley Packet Filter, is a kernel technology available since Linux 4.4.
It lets developers run programs without adding additional modules or modifying the kernel source code. Think of it as a lightweight, sandboxed virtual machine (VM) within the Linux kernel that lets you run Berkeley Packet Filter (BPF) bytecode that uses certain kernel resources.
Utilizing eBPF removes the need to modify the kernel source code and improves the software’s capacity to use existing layers.
eBPF has fundamentally changed how concepts like observability, security, and networking are delivered within an app.
How does eBPF work?
It’s important to understand that eBPF consists of small programs written in a restricted subset of the C programming language called eBPF programs.
These programs allow an application to access hardware and services from the Linux kernel and enhance debugging and networking. Additionally, the restricted nature of the language ensures that the programs are safe to execute within the kernel without causing crashes or security issues.
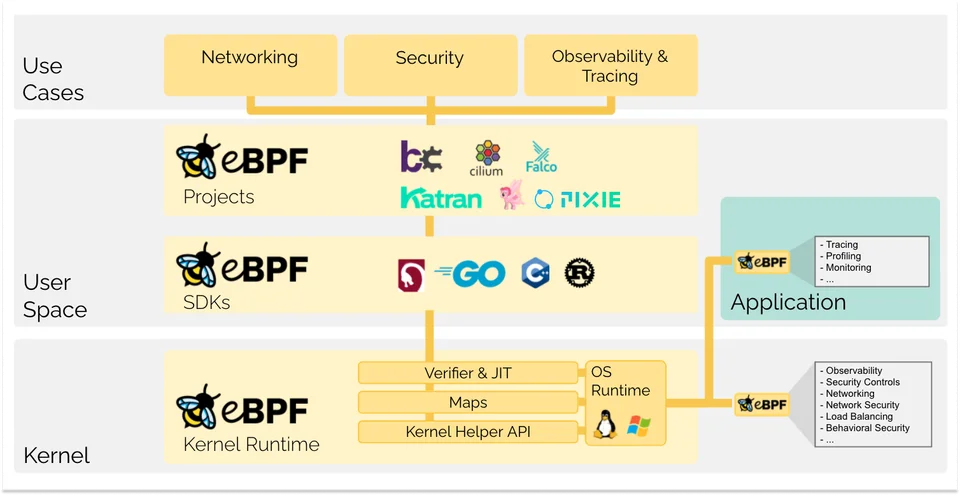
What is the architecture of eBPF?
The architecture of eBPF includes the following:
Predefined Hooks
eBPF programs run according to events that trigger them when an application passes a threshold known as a hook point. Hooks are predefined and can include network events, system calls, function entry and exit, and kernel tracepoints. kprobes, uprobes are custom hooks that can be defined on kernel functions (for kprobes) and user space functions (for uprobes).
Program Verification
Once a hook is identified, the BPF system call loads the eBPF program into the Linux kernel.
This involves using an eBPF library. When a program is loaded into the kernel, it has to be verified to ensure it is safe to run. This is done by guaranteeing several measures, such as:
- The program can only be loaded by a privileged eBPF process.
- The program won’t crash the system.
- The program will always run to completion.
eBPF Maps
An eBPF program must be able to store its state and share collected data. eBPF maps help programs retrieve and store information according to various data structures. Users can access eBPF maps via system calls from both eBPF programs and applications.
Helper Calls
It’s important to note that an eBPF program cannot call into a kernel function. This is because eBPF programs must maintain compatibility and avoid being bound to specific versions of the kernel.
Thus, eBPF programs use helper functions, essentially APIs provided by the kernel, to make function calls. These helper calls allow programs to generate random numbers, receive current times and dates, access maps, manipulate forwarding logic and network packets, and more.
Function and Tail Calls
These calls make eBPF programs composable:
Function calls enable functions to be defined and called in a program. Tail calls allow the execution of other eBPF programs. Additionally, they can also change the execution context.
What are the use cases of eBPF?
Now that we’ve established a basic understanding eBPF use cases, it’s essential to understand how developers can effectively use it in their applications. Therefore, consider the following use cases and adapt to your business requirements accordingly.

Observability and Monitoring
The generation of visibility events, collection, and in-kernel aggregation of custom metrics based on many sources is possible with eBPF.
This increases the visibility that might be attained while drastically reducing the overall system overhead. This is achieved by collecting only the required visibility data and producing histograms and similar data structures at the source of the event rather than depending on the export of samples.
Examples include:
- System Resource Monitoring: Monitoring CPU, memory, and disk usage for performance tuning.
- Application Bottleneck Identification: Identifying performance bottlenecks within applications.
Tracing and Profiling
You can attach eBPF programs onto a tracepoint to bring about high visibility into the runtime behavior of applications. This gives unique and powerful insights to troubleshoot system performance issues.
Examples include:
- System Profiling: Profiling system calls, kernel functions, and process activity for performance analysis.
- I/O Profiling: Profiling disk I/O, file system operations, and network I/O.
- Application Profiling: Profiling user-space applications to identify bottlenecks and performance issues.
Security
Extending the basic capabilities of seeing and interpreting all system calls and providing packet and socket-level views of all networking operations enables the development of revolutionary approaches to system security.
Typically, entirely independent systems have handled different aspects of system call filtering, process context tracing, and network-level filtering. On the other hand, eBPF facilitates the combination of control and visibility over all aspects. This allows you to develop security systems that operate with more context and improved control.
Examples include:
- Malware Detection: Detecting and preventing malware activities through behavioral analysis.
- Security Monitoring: Real-time monitoring and alerting for security events and anomalies.
Networking
Combining efficiency and programmability makes eBPF a good candidate for all networking solutions’ packet processing requirements. The programmability of eBPF provides a means of adding additional protocol parsers and smoothly programs any forwarding logic to address changing requirements without ever exiting the Linux kernel’s packet processing context. The effectiveness offered by the JIT (Just-in-Time) compiler offers execution performance near that of natively compiled in-kernel code.
Examples include:
- Packet Capture: Capturing and analyzing network packets for debugging and monitoring.
- Firewall and Security: Implementing custom firewalls, intrusion detection, and security monitoring.
- Network Traffic Analysis: Collecting and analyzing network statistics, such as bandwidth usage and connection details.
Helios leverages both eBPF and OpenTelemetry and provides Dev, Ops, and Sec teams with runtime insights, helping them reduce MTTR, shorten troubleshooting time, improve reliability, and prioritize vulnerabilities in distributed applications.